Imagine a bustling digital marketplace hidden just beneath the surface of the internet—a place woven with layers of encryption, anonymity, and secrecy. It’s a realm where traditional domain names give way to cryptic, seemingly random addresses ending in “.onion.” These are the Tor hidden services, known colloquially as the dark web’s hidden corners. While many picture them as shadowy and stagnant, a surprising shift is underway. New hidden services are not only emerging but gaining notable traction, reshaping the landscape of privacy, censorship resistance, and anonymous communication.
What is driving this fresh wave of hidden Tor services? Why are they capturing attention now, in 2025, when privacy tools have never been more scrutinized? To understand this momentum, you have to look beyond the old stereotypes and explore these sites’ evolving missions, technologies, and communities.
In This Article
Why Tor Hidden Services Still Matter
It’s easy to assume that with mainstream encrypted messaging and VPN popularity rising, Tor hidden services would be fading into obscurity. But the opposite is true. Their resilience and unique architecture offer benefits unmatched by conventional privacy tools.
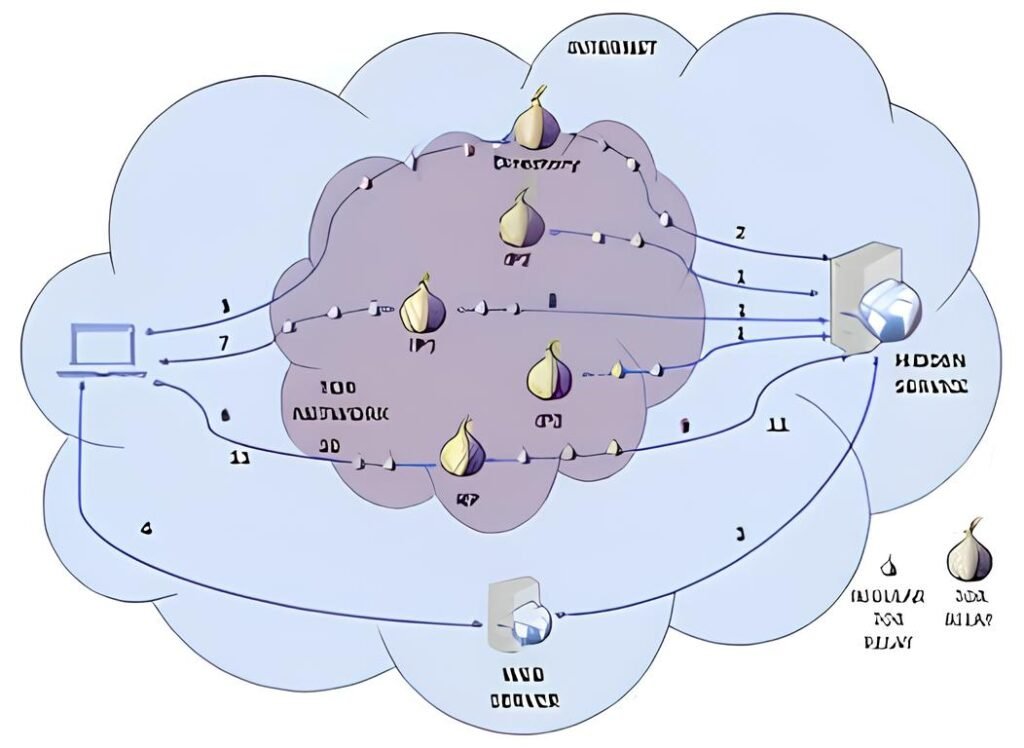
Unlike clearnet websites, Tor hidden services hide their server locations and operate exclusively within the Tor network. This design makes censorship and takedown efforts significantly harder. For journalists, activists, and whistleblowers in oppressive regimes, hidden services remain critical lifelines, safeguarding both sources and platforms.
Furthermore, the evolution of surveillance tactics—leveraging AI, metadata analysis, and sophisticated network attacks—has made simply using Tor a baseline rather than an advantage. Hidden services adapt by integrating advanced cryptographic safeguards and decentralization strategies that increase trust and anonymity.
New Technology Shaping Tor Hidden Services
The tech powering .onion sites is far from static. Recent years have introduced major updates like Tor version 3 addresses, which replaced the older, shorter version 2 links, offering stronger cryptographic primitives and longer addresses. This enhances security but also raises usability challenges due to their complexity.
In response, new projects combine decentralized DNS alternatives with Tor onion services, allowing users to discover hidden services without relying on brittle, centralized indexes prone to censorship or seizure.
Another leap comes from improved uptime and availability techniques. Many cutting-edge services deploy multiple mirrors—redundant copies hosted across geographically dispersed servers—that help maintain access even if one or more are compromised. This redundancy, coupled with automatic failover, is essential in volatile environments.
Hybrid hosting models are also rising. These use a mix of Tor relays and traditional VPNs or proxy chains to balance latency, access control, and anonymity. Developers continue to innovate around hosting options, including self-hosted VPS solutions, emphasizing secure Onion hosting practices that limit traces and vulnerabilities.
Popular New Categories of Hidden Services
What kind of hidden services are gaining traction today? The ecosystem is diversifying in compelling ways beyond the well-known darknet marketplaces.
- Privacy-first crypto exchanges: These platforms emphasize zero-knowledge proofs and decentralized escrow, enhancing confidentiality for traders.
- Encrypted social forums: New forums emerge focused on niche interests like human rights activism, decentralized governance, or privacy education.
- Anonymous publishing platforms: These portals provide censorship-resistant spaces for journalists and whistleblowers, guarded under robust OPSEC frameworks.
- Secure chat and collaboration tools: Hidden services that offer real-time encrypted messaging and project management, often open-source and built to run completely within Tor.
These categories reflect a shift from illicit associations to privacy-first, decentralized utilities. The rise of privacy-enhancing technology innovations such as multi-party computation and hardware-backed attestation means new services can stay private without sacrificing functionality.
How Communities Fuel These Hidden Networks
One surprising factor behind the growth of new Tor hidden services is community-driven momentum. Unlike commercial ventures, many hidden sites flourish through the enthusiasm and trust of committed user bases.
Developers often collaborate openly through forums and encrypted channels, sharing best practices for secure deployment, OPSEC, and anti-sybil strategies. Peer-reviewed cryptographic improvements circulate rapidly, creating a feedback loop of innovation driven by privacy advocates.
Moderated darknet forums, despite their risks, have also improved governance models, establishing clearer community guidelines and verification methods to minimize scams and honeypots. This development strengthens trust, crucial for onboarding new users.
If you plan to explore newer hidden services, consider joining privacy-focused communities that share vetted onion addresses regularly. But always remember to keep your operational security tight and practice good anonymity habits.
Challenges and Risks Facing Hidden Services
Growth brings attention—and with attention comes risks. Despite innovations, hidden services confront constant threats from law enforcement takedowns, internal scams, and technological limitations.
One persistent problem is the risk of deanonymization. Flaws in configurations or user mistakes can expose server IPs or user data. Attackers employ advanced timing correlation attacks that compare traffic entering or exiting the network, sometimes combined with AI-driven behavioral analysis.
Moreover, hosting providers, even when anonymous, may be compelled to cooperate with requests or seizures. This vulnerability drives many operators to use decentralized hosting frameworks and encrypted hosting—with varying degrees of success.
There’s also a usability hurdle: the complexity of Tor .onion URLs can easily lead to mistakes, typosquatting, or malicious redirects. Users must be vigilant about verifying addresses, especially with the rise of fake or cloned sites meant to steal credentials or track visitors.
Be wary of newly popular hidden services lacking a verifiable reputation. Scams remain rampant, and operational clips can accidentally expose your identity. Use strong digital hygiene and never reuse credentials.
Tips for Safe Access to Tor Hidden Services
Navigating the new wave of hidden services safely requires deliberate care. Here are key guidelines:
- Always use the official Tor Browser to access .onion sites—avoid browser extensions or third-party apps that may leak data.
- Keep your software updated—Tor Project releases frequent security improvements, and using outdated clients opens risks.
- Verify .onion addresses carefully, using trusted sources or cryptographic signatures when available, to avoid phishing or typosquatting.
- Consider combining Tor with a reputable VPN for layered privacy. You can learn which providers are best suited in our guide on the best VPNs for Tor in 2025.
- Use disposable pseudonymous identities for communication and transactions, avoiding cross-service profile overlaps that can compromise anonymity.
- Engage with communities that emphasize OPSEC and have clear guidelines on safety, reporting, and anonymity practices.
While no method guarantees complete safety, layering these strategies can drastically reduce your risk when exploring hidden services.
Building a Long-Term, Secure Relationship With Hidden Services
Growth of new Tor hidden services signifies not only technological change but a cultural rekindling—an opportunity to reclaim privacy and security in an increasingly surveilled online world. But this evolving landscape demands thoughtful preparation and continuous learning.
Explore with curiosity, but always place security first. As the digital underground expands and matures, staying informed helps ensure that the hidden web remains a refuge rather than a trap.